ANTONIO LÓPEZ | Tungsteno
The rise of teleworking has been one of the most tangible consequences of the pandemic. We first noted the emergence of two models, virtual and mixed, and analysed the challenges of maintaining teleworking when the current global health emergency is over. Then we took a look at the most important digital tools for adapting to this new era of work. And now we examine one of its main, more intangible, weaknesses: ensuring security.
On 7 May, a group of hackers achieved something unprecedented in history: paralysing an oil pipeline that distributes 45% of the fuel consumed on the east coast of the US. The "hijacking" of the digital infrastructure that controls the Colonial Pipeline led those in charge of this critical facility to completely shut down its operation for days, resulting in disruptions to flight schedules and supply shortages at gas stations in the southeastern US. Many people rushed to hoard gasoline. 87% of filling stations in Washington D.C. ran out of fuel on 14 May and prices soared to a seven-year high.
The Darkside hacker group, which claimed responsibility for the ransomware attack, demanded a ransom of $5 million in cryptocurrencies in exchange for unlocking the pipeline. This event, along with other recent ones such as the latest massive theft of Facebook data or the cyberattack suffered by the Spanish Public Employment Service (SEPE), has once again brought the risks of hyperconnectivity back to the table.
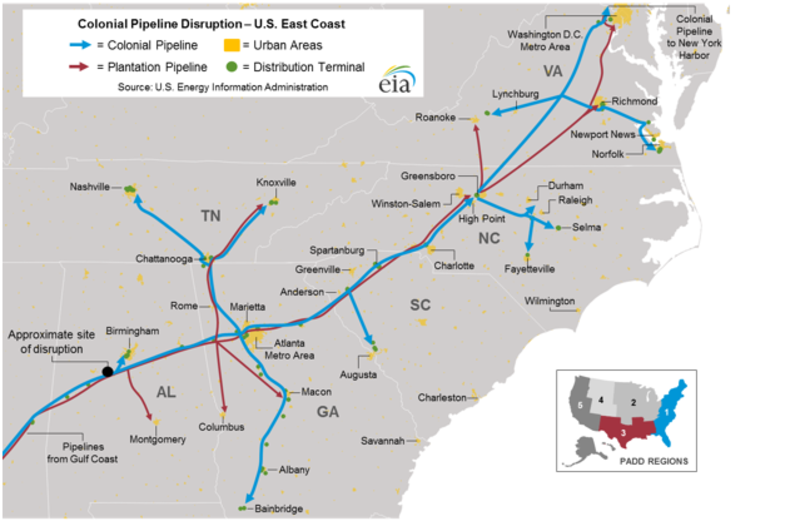
On May 7, a group of hackers paralyzed an oil pipeline that distributes 45% of the fuel consumed on the east coast of the United States. Credit: U.S. Energy Information Administration.
The risks of connected infrastructures
The digital transformation that is affecting all types of sectors has reached industries as apparently anchored in the 20th century as the oil industry. Despite these appearances, there are already modern pipelines such as Colonial, which use a complex computer network of pressure sensors, thermostats, valves and pumps to remotely operate this large piece of infrastructure, detect faults and collect data in order to optimise its operation. While savings and efficiency are maximised, so too are opportunities to hack the system.
Such cyberattacks are not common since the level of protection is high. But where there is connectivity, there is vulnerability, as Jon Niccolls of Check Point Software reminded the BBC: "Some of the biggest attacks start with an email. A Colonial employee could have been tricked into downloading a piece of malware," said the cybersecurity expert, who believes it is more likely that hackers gained access to the pipeline's control system through the administrative side of the company.
Threats of this kind have multiplied in recent months. At the end of the first lockdown, Interpol warned about the alarming increase in cyberattacks brought about by the COVID-19 pandemic and teleworking. "The increasing reliance on the Internet by people around the world also provides new opportunities for criminals, as many businesses and individuals are not ensuring that their cyber-defences are up to date," said Interpol Secretary General Jürgen Stock, who urged closer cooperation between the public and private sectors to contain this risk.

Interpol has warned of an increase in cyber attacks during the coronavirus pandemic. Credit: Interpol.
The wave of cyberattacks brought by the pandemic
Cybercriminals then took advantage of "the fear and uncertainty caused by the resulting socio-economic instability" to intensify malware and ransomware attacks. They also carried out frauds, promoted malicious domains ostensibly related to information about the pandemic, and spread fake news. Phishing attempts disguised as supposedly official Netflix password reset emails, cyberattacks on hospitals or fake job offers have also been detected.
Taken to the world of work, this general threat made companies aware of the sudden increase in their cyber vulnerability: "We have gone from having one company with 50 computers to having 50 offices, one in each house, which increases the risk because we also have more devices connected at home. In fact, we detected a television that was capable of crashing the entire server due to a conflict with updates," Fernando González, CEO of the Megastar consultancy, told the newspaper Heraldo de Aragón.

During the pandemic, malware and ransomware attacks, scams or phishing attempts have intensified. Credit: Unsplash.
Javier Serrada, head of projects and pre-sales at the consultancy Gotor Comunicaciones, calls for computer security awareness to be broadly incorporated into occupational risk prevention and recalls the three pillars of cybersecurity: confidentiality, veracity and availability. "We must ensure that not everyone can access certain types of information, and that when they do, it is truthful, it has not been manipulated by a third party or has disappeared," he says.
Business security collides with home networks
The password barrier becomes a crucial firewall. Forgetting them or not updating them regularly can have serious consequences in terms of cybersecurity, which is why one of the most sensitive issues for companies, and one of the most tedious for virtual workers, is password management. Services such as Bitwarden or LastPass make it possible to store all of a user's passwords in the same secure database. They also speed up the registration process for new applications and synchronise the updating of passwords across multiple devices.
The report Cybersecurity Trends 2021, prepared by ESET, points to other solutions: "Some of the baseline security measures taken for granted in the office must be compensated for at home, such as requiring home workers to use multi-factor authentication or a VPN to access internal networks."
Still, it is difficult to guarantee the absence of security breaches. Even in the ideal case where remote workers always use company-delivered devices and follow these protocols, the security of their own home Wi-Fi networks—an increasingly open avenue for cybercriminals due to the rise of home automation devices—should also be verified.
· — —
Tungsteno is a journalism laboratory to scan the essence of innovation. Devised by Materia Publicaciones Científicas for Sacyr’s blog.
